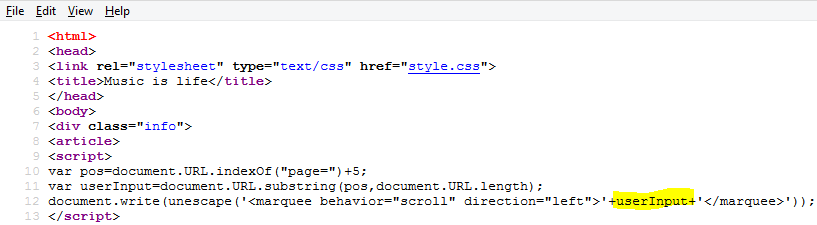
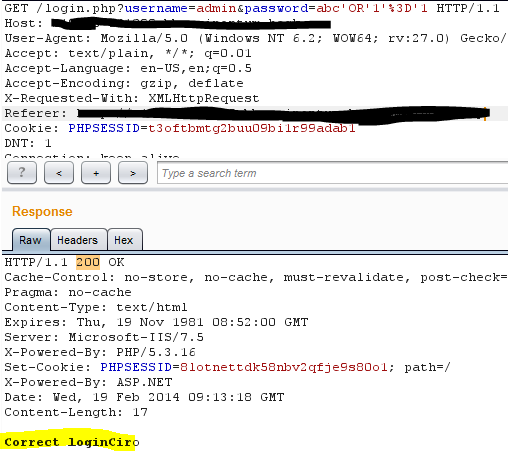
Introduction:
w3af (Web Application audit and attack framework) is a web
applications framework for auditing and exploitation. In this article we will
demonstrate how to scan application(s) using CLI, overview of various plugins
and inter-communication among the plugins.
Features:
W3af plugins communicate with each other i.e. discovery
plugin identify different application URLs and passes the result to the audit
plugin, which further uses these URLs to find vulnerabilities. W3af has
features like fuzzing and manual request generator and also be configured as man-in-the-middle
proxy.
Plugins:
To open up the console type the following command. It may ask you to update the W3af repository.
Figure 1: W3af
Console
Now type command = ‘help’ to provide details of available features.
Figure 2: W3af help
The command, ‘plugins’,
can be used to list the available plugins in the framework. We can further explore
available options within each plugin. keys
command can be used to see list of short cut.
Figure 3: Keys
command
Enter the plugin name followed by help (i.e. help PluginName) to find details about
the plugin. Example: help Discovery will fetch the details
regarding Discovery plugin.
Figure 4: Discovery
plugin
There are 9 plugins in the w3f framework. A user can enable
one or more plugin(s) as per their need. In this section, we will go over some
of them.
Discovery:
Discovery plugin crawls and identifies URLs/forms
with in the web application. This information is used detect web
vulnerabilities. This plugin has features like spiderMan, hmap, webspider etc. We can type ‘discovery’ to check the options in this plugin.
Figure 5: List of
discovery plugins.
To get further information on the certain plugin, we can
type discovery desc ‘pluginaname’. For
example, discovery desc xssedDotCom, would
retrieve us help on xssedDotCom plugin.
Figure 6:
XSSedDotCom Description
Other commonly used commands are listed below:
To enable more than one plugin: discovery plugin1, plugin2
To enable all plugins: discovery all
Removes all enabled plugins: discovery !all
List enabled plugins: list discovery enabled
Figure 7: Some more
commands
Audit: Audit plugin detects vulnerabilities on the URL’s
identified by discovery plugin. This plugin injects various set of input
strings and verifies the responses. It can identify vulnerabilities like SQL injection,
XSS, CSRF etc. To retrieve the details about XSS feature in this plugin, we can type: audit desc xss
Figure 8: XSS Plugin
description
The screen shot above shows that there are two configurable
parameters available for XSS. We can set numberOfChecks
by typing the below command.
Figure 9: Configure
XSS parameters
Grep: The grep
plugin works like passive scanning and finds issues by analysing request/response.
It can look for information like credit card number, PII details and forms with
file upload functionality etc. It is essential that we enable discovery plugin
before using grep.
Figure 10:
Grep Plugin for file upload
Output: The output plugin can help us produce
results in different formats. Currently the supported formats are XML, Console,
html, text etc. Users can also configure parameters like filename, verbosity
level etc.
In next post will see how to configure basic scan using some common plugin and identify vulnerability like XSS.