In this post will talk about DOM Based XSS which is also known as type-0 XSS. DOM XSS is very difficult to find using scanner and most of the time scanner tend to give false positive.
In DOM based XSS attacker modifies object of Document Object Model. Modifying DOM environment does not change response but the client side code contained in the page executes differently due to the malicious modifications that have occurred in the DOM environment.
In the other form of XSS (stored and reflected) payload is executed in the response due to server side flow contrast to DOM based XSS.
Let's see an example.
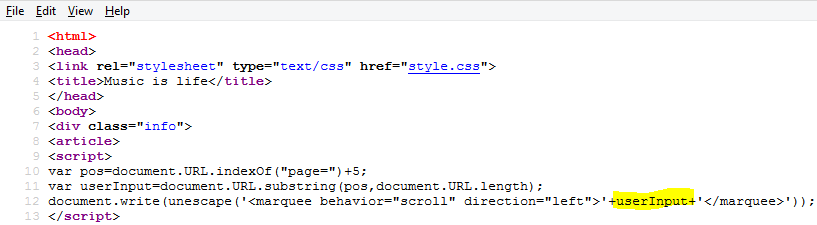
As we can see in below screen shot website having parameter called "page".
And value to this parameter appears on website as a marquee. This value can be modified by attacker.
Now let's insert XSS payload <script>alert('XSS')</script> to the "page" parameter. And attacker can also craft URL with payload <script>alert(document.cookie)</script> and send it to victim to get session cookie.
There are few guidelines for the developer to follow to avoid DOM based XSS. Any Untrusted data should not be rendered instead use encoding or sanitize input. Also avoid HTML rendering methods like document.write & element.innerHTML.
Reference: https://code.google.com/p/domxsswiki/wiki/Introduction


Hi Bhaumik, Your blogs and videos always found useful. When I am not able to understand any topic or vulnerability, I look for your videos or blogs, and then I understand the key concept of the vulnerability. Please continue your blogs and videos as well, your content always help individuals like me.
ReplyDelete